Automating Suites¶
OWASP ZAP (Free, Open-Source)¶
BurpSuite¶
- https://tryhackme.com/room/burpsuitebasics (free)
- https://tryhackme.com/room/burpsuiterepeater (vip)
- https://tryhackme.com/room/burpsuiteintruder (vip)
- https://tryhackme.com/room/burpsuiteextender (vip)
- https://tryhackme.com/room/burpsuiteom (vip)
- https://tryhackme.com/room/rpburpsuite (vip)
Comparision OWASP ZAP vs BurpSuite¶
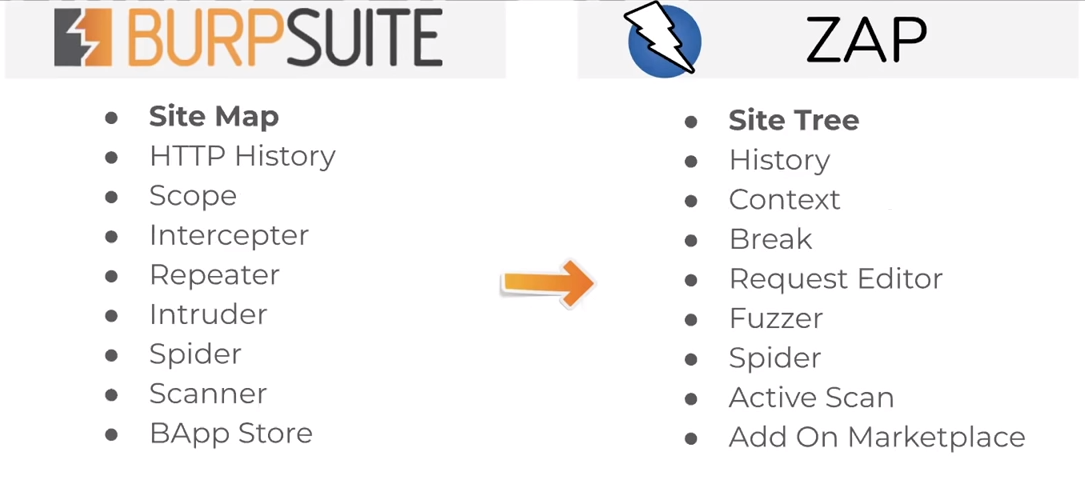
| Feature | Burp Suite Community Edition | OWASP ZAP | Burp Suite Pro |
|---|---|---|---|
| Web Application Scanning | Not Available | Available with basic security vulnerabilities | Available with quality security vulnerabilities |
| Intercepting Feature | Available | Available | Available |
| Fuzzing Capabilities | Available | Available | Available |
| Encoder and Decoder | Available | Not Available | Available |
| Cost | Free | Free | Paid Subscription - Advanced Functionality ($399 per year) |
| Documentation | Extensive documentation available | Little documentation available | Extensive documentation available |
| Spider | Available | Available | Available |
| Updates | Available | Available | Available |
| Extensions | Less Options Available | No provision for enhance functionality | Available |
| Coverage | Medium coverage | Less coverage | Extensive Coverage |
| False Positive | Less | More | Less |
| Session Token Entropy Analysis | Available | Not Available | Available |
| Comparison Feature | Available | Not Available | Available |
Credits: https://allabouttesting.org/burp-suite-vs-owasp-zap-which-is-better/
Attacking modes¶
-
Sniper - The most popular attack type, this cycles through our selected positions, putting the next available payload (item from our wordlist) in each position in turn. This uses only one set of payloads (one wordlist).
-
Battering Ram - Similar to Sniper, Battering Ram uses only one set of payloads. Unlike Sniper, Battering Ram puts every payload into every selected position. Think about how a battering ram makes contact across a large surface with a single surface, hence the name battering ram for this attack type.
-
Pitchfork - The Pitchfork attack type allows us to use multiple payload sets (one per position selected) and iterate through both payload sets simultaneously. For example, if we selected two positions (say a username field and a password field), we can provide a username and password payload list. Intruder will then cycle through the combinations of usernames and passwords, resulting in a total number of combinations equalling the smallest payload set provided.
-
Cluster Bomb - The Cluster Bomb attack type allows us to use multiple payload sets (one per position selected) and iterate through all combinations of the payload lists we provide. For example, if we selected two positions (say a username field and a password field), we can provide a username and password payload list. Intruder will then cycle through the combinations of usernames and passwords, resulting in a total number of combinations equalling usernames x passwords. Do note, this can get pretty lengthy if you are using the community edition of Burp.